Our central London apartments have 1GB fibre connections with Hyperoptic which are reliable and fast. We get the speeds advertised, and at one our flats it is even a little faster. Ping is time 1ms. With such fast speeds, upload as fast as download, it is tempting to run servers at home and run a private cloud. The snag is the devices at home are not reachable from the internet using IPv4; the home routers are behind CGNAT, just as phone companies do in order to share the rationed IPv4 addresses and protect their network. You can pay Hyperoptic and other fibre companies extra each month for a fixed IPv4 address that is then reachable from the outside using IPv4. You may not need to. Better to use IPv6 anyway.
Home devices can be reached by IPv6 addresses from the internet which when calling from an IPv6 enabled network. IPv6 is fixed and we are given a whole reachable subnet. Then we can set the home router’s IPv6 filter; that is open pinholes or IPV6 filter rules to local devices’ IPV6 address and ports we want. We can now have multiple reachable devices from the internet and even using the same port, say port 443, as there is no address sharing (NAT).
There has been a snag using Hyperoptic routers, even their latest H3600 router when it comes to IPv6 routing. Many customers give up and buy their own routers. The Hyperoptic router manual has incorrect instructions for IPv6 filters. The first thing to note that the “LOW” firewall setting does not seem to affect IP4 blocks and port forwarding rules, but low does open all IPv6 devices on the LAN, so an open port of any device is reachable on the internet in IPv6 addresses. Not a good idea. But middle and high settings are fine, I set mine to high so all ports are closed unless defined by the filter rules.
Now adding filter rules was a pain, and it took me a day to realise why some rules worked and others did not. The IPv6 filter rule secret is NOT to declare the incoming port. It you put a number in there the rule is ignored.
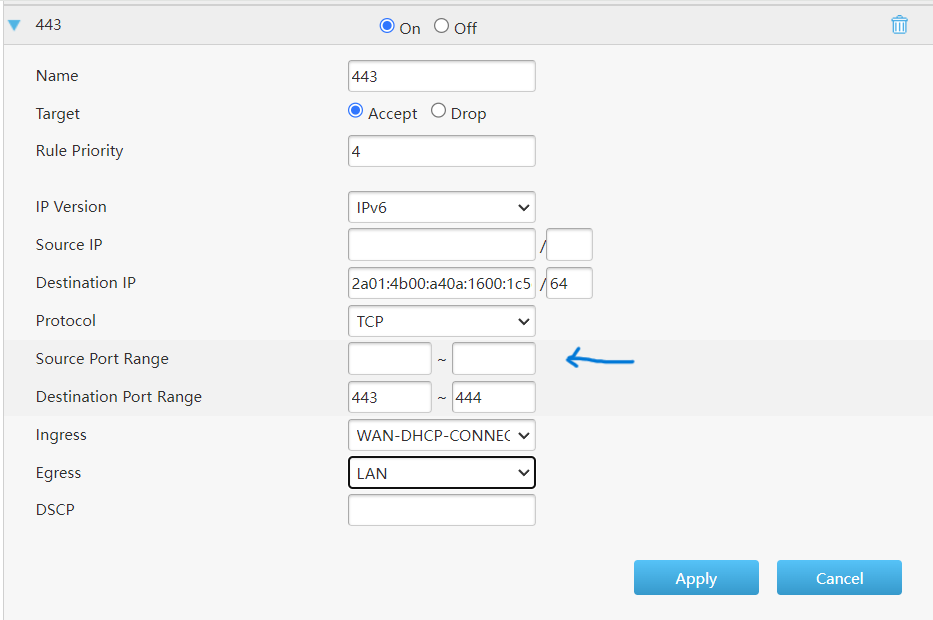
So all fixed and I do not need to buy a new router.
By the way if you port-forward 443 it stops Hyperoptic from accessing the device. Not that their support is of any use when it comes to anything technical.
Connection works from IPv6 enabled networks away from home. It does not always work from some workplaces or from many phones because still some ISPs still use IPv4 only routing. To solve this I use another server (my VPS) that has fixed IPv4 and IPv6 connections I use the VPS as a middle man to “cat” the connection from IPv4 to an IPv6 address. I can access home systems anywhere and can give my home machines domain names IPv4 and IPv6 with DNS entry. On this middle machine, a Linux site (a VPS) I use SOCAT command with the IP and ports I want like this:socat TCP4-LISTEN:9831,fork,su=nobody TCP6:[2a01:4b02:a40a:4b10:af9b:c59c:b1b8:2e7x]:2529. Connecting to MyVPSserver:9831 using IPv4, connects to my a home device on IPv6:2529. I run a VPN though it (SoftetherVPN). It’s magical (don’t forget to open the port on the middle server if needed). It is very fast, I do not notice any degradation. When using Myvpserver domain I set DNS A (IPv4) to the VPS server and DNS AAA (IPv6) direct to the home device IPv6 address.
As it happens I found that if you have two places with Hyperoptic fibre connections you can access the other by using the internal Hyperoptic IPv4 addresses that are given to their routers (in 10.0.0.0 range). These internal Hyperoptic IPv4 addresses seem fixed. These IPs have not changed over multiple reboots.
The other approach to reach your server is to use a reverse SSH tunnel from home server to one with a fixed IP such as a VPS. Using a Softether VPN ( the easiest of VPNs to set up) we can have full access to the network. To automate this I use autossh, set up in /etc/rc.local rc.local is now depreciated but I find it easier.
autossh -M 0 -N -f -o “ServerAliveInterval 30” -o “ServerAliveCountMax 3” -o “PubkeyAuthentication=yes” -o “PasswordAuthentication=no” -i /root/.ssh/id_mykey -R 50020:localhost:5555 user@mydomain -p 2526 & This connects the remote, behind the firewall machine (usually a Raspberry) Pi to my VPS SSH port 2526 using the key id_mykey. The VPS now has the the 50020 as a tunnel back to the remote machine’s Softether default port 5555. A Profile on Softether client on any device can be set to connect to mydomain port 50020 (if port open or localhost:50020 to tunnel the port via SSH)
I was also using the reverse tunnel to connect to a 4g router. This is a 4g dongle attached to Raspberry PI as part of a remote ham radio project. I have no space in London for antenna. I was to run Remote Rig though the tunnel but 4g latency was the problem.